Defining Cybersecurity Control
Control is a critical part of Cybersecurity, but defining it can be difficult
By: Owahn Bazydlo
Published, October 14, 2022
Defining control through the lens of Cybersecurity is difficult because control can be applied multiple ways. When asked to define control, the answer is typically clear to the individuals using the term. However, their answers are guided by their perspective on Cybersecurity. Some will use the term to talk about a technology solution, while others will discuss organizational compliance or standards.
No framework, technology, standard, process, or other element of control is enough on its own to define Cybersecurity control. However, when you connect these control elements together the control becomes clear. The importance of defining control for your organization is to ensure that the elements of control are connected to each other. The more control elements are connected, the more efficient and effective the individual control will operate.
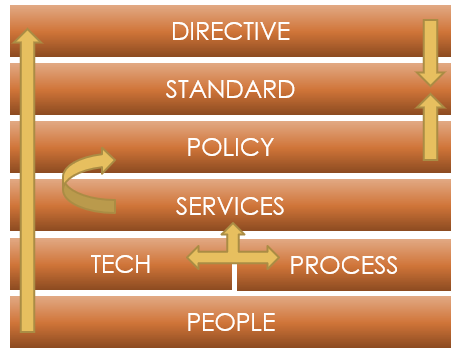
We define control through seven elements to maximize your organizations understanding of origin, definition, enforcement, and operational use.
Understanding the Seven Elements of Control:
Directive: The directive segment represents the various drivers that may influence or direct an organization’s Cybersecurity program. These directives may include but are not limited to applicable regulation, laws, industry frameworks, or internal drivers such as organizational mandates or program strategies.
Standards: Standards are the organizational rules that identify what can and cannot occur on your organizations network. Standards identify the approved operating state for an organization and can guide how a policy should be enacted.
Policy: Policies are general documents that outline how an organization intends to operate and will usually speak to general Cybersecurity objectives. However, policies may also include specific mandates or enforcement mechanisms.
Services: Services are collection of Tech, Process and People that arrange to provide a service to the organization. These services may tie directly to frameworks, policies, and standards, or they may exist independently based on an organization’s need and maturity.
Technology: Technology represents the technological controls that are in place to help either enforce, detect, or enrich data and drive an outcome.
Process: Processes represent the steps taken to generate some designed outcome. Processes and tech are tightly coupled; however, they can operate independently of each other, and depending on capability can be mutually exclusive elements of the framework.
People: People represent the individuals who are charged with executing the control. The people will span all elements of the framework; however, this section is meant to align ownership and accountability of a control to a specific individual or group.
Applying the Seven Elements of Control
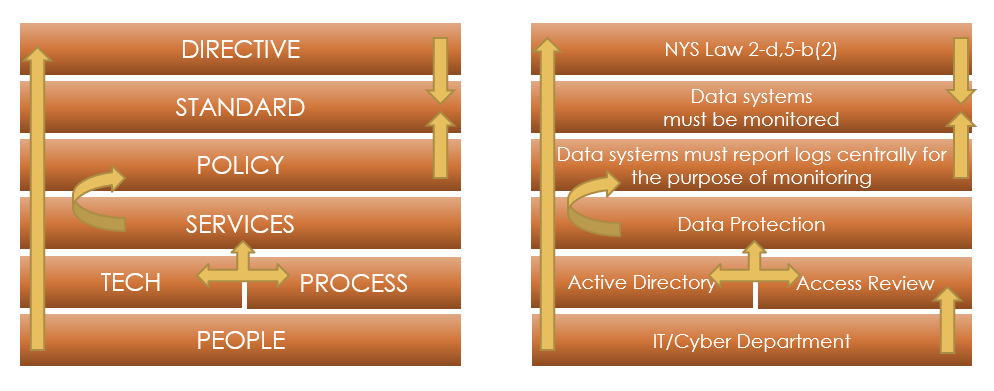
The example below shows how using the seven elements of control fully captures how control elements are applied to address the requirement of NY Law 2-d, 5-b(2) a Law that establishes data privacy and security for New York Schools. Populating the elements of the control stack to meet this law helped to connect this control from its origin (legal mandate) down through the people responsible (Ownership) for ensuring the control is applied holistically.
DIRECTIVE: NYS Law 2-d,5-b(2) Mandates that School’s data systems be monitored.
STANDARD: This can be translated into an internal standard that states: “All Data systems that house student data MUST be monitored for inappropriate or unauthorized access”
POLICY: The policy can then enforce this: “Any system that is not monitored may not house Student data. Any system that has student data must send its access logs to a central location for evaluation and monitoring.
SERVICES: A service can be chartered called “Data Protection” One of the functions of the Data Protection team could be “Access Monitoring to data systems”.
TECHNOLOGY: Technology can be used to log, monitor and reviewed access using Microsoft Active Directory.
PROCESS: At regular intervals, a process can be used to review these logs to ensure that individuals who are not permitted to access this data are not accessing it.
PEOPLE: This process can be carried out by members of the IT/Cybersecurity staff.
We at TALAS Security are passionate about control. We hope this information has helped you understand how you can organize your controls in a way that is easy to understand, define and enforce. Our mission is to help organizations enable their Cybersecurity advantage and making Cybersecurity accessible is one of the ways we achieve that mission.